| CPC H04L 63/102 (2013.01) [H04L 63/0236 (2013.01); H04L 63/0245 (2013.01); H04L 63/145 (2013.01); H04L 63/20 (2013.01); H04L 67/06 (2013.01)] | 15 Claims |
|
1. A computer-implemented method executed by a hardware processor for securing a collaboration tool against unauthorized data exfiltration, including:
setting policies applicable to exfiltration of files to users in an external guest user category and uploading of files by the users in the external guest user category;
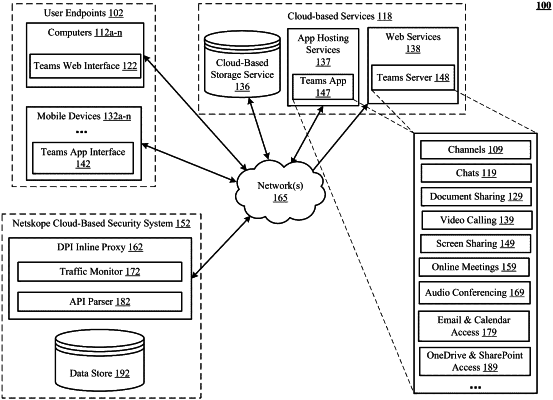
using an in-line proxy that intercepts a pair of communication platform add request and add response API messages for adding an invited user to a team, wherein the add response message contains an #EXT# tag identifying the invited user as belonging to the external guest user category, but the add request message itself identifies the invited user without indicating whether the invited user belongs to the external guest user category;
in response to determining, by the in-inline proxy, that the add response includes the #EXT# tag, storing metadata in a storage that is external to the communication platform, the metadata identifying the invited user as belonging to the external guest user category for application of the policies applicable to the external guest user category;
using the in-line proxy to intercept a particular pair of a request and response of the communication platform for file transfer involving a particular user and a referenced file, and to identify the particular user, wherein neither the request nor the response for file transfer in the particular pair indicate whether the particular user belongs to the external guest user category;
looking up the particular user in the externally stored metadata and identifying the particular user as belonging to the external guest user category;
looking up at least one policy of the policies applicable to the external guest user category and applying the at least one policy to the particular request for file transfer;
responsive to the at least one policy, invoking deep packet inspection (abbreviated DPI) and detecting that the file referenced in the particular request contains sensitive information not permitted by the at least one policy to be transferred to the particular user in the external guest user category; and
blocking transfer of the file that contains sensitive information.
|