| CPC H04L 63/102 (2013.01) [G06Q 20/40 (2013.01); G06Q 20/4016 (2013.01); H04L 63/0876 (2013.01); H04L 63/08 (2013.01)] | 20 Claims |
|
1. An authorization apparatus for security management of a plurality of interactions, comprising:
a memory, associated with a server, operable to:
store interaction information associated with one of one or more users and a first entity;
store entity account data for a plurality of entities; and
a processor, associated with the server, operably coupled to the memory, configured to:
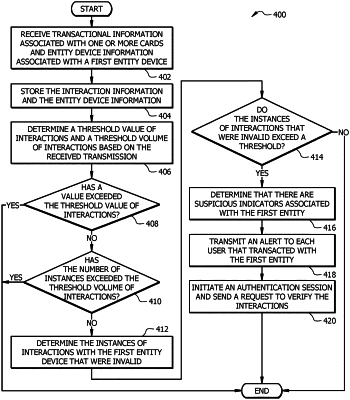
receive the plurality of interactions, each interaction comprising the interaction information associated with one of the one or more users and the first entity;
determine a threshold value of the plurality of interactions and a threshold volume of the plurality of interactions for each one or more users received by the plurality of entities based on the stored entity account data;
determine that a value of each of the received plurality of interactions has not exceeded the threshold value of the plurality of interactions;
in response to determining that a value of each of the received plurality of interactions has not exceeded the threshold value of the plurality of interactions, determine that the plurality of interactions has not exceeded the threshold volume of the plurality of interactions;
determine a number of instances of the plurality of interactions that were invalid;
determine that the number of instances of the plurality of interactions that were invalid exceeds a threshold; and
in response to determining that the number of instances of the plurality of interactions that were invalid exceeds the threshold, determine that the first entity is associated with suspicious indicators, wherein suspicious indicators comprise a category within data classification utilized by the authorization apparatus to categorize received data by the processor, wherein suspicious indicators signal that there is unauthorized activity associated with the first entity.
|