| CPC H04L 63/101 (2013.01) | 21 Claims |
|
1. In a digital medium environment for graph-based access control, a method implemented by at least one computing device, the method comprising:
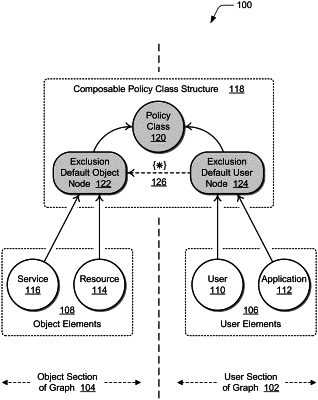
generating a next generation access control (NGAC) graph configured with multiple policy classes as enforceable access criteria by which users are allowed or denied access to resources, the NGAC graph having a bifurcated structure with a user section that includes the users modeled as user elements and an object section that includes the resources modeled as object elements;
modeling policy binding nodes as user attributes in the user section of the NGAC graph, the policy binding nodes modeled for each of the multiple policy classes and each of the policy binding nodes assigned to a corresponding one of the multiple policy classes, the NGAC graph being a directed acyclic graph (DAG structure generated and stored as a bi-directional graph structure facilitating evaluation of the NGAC graph with a graph evaluation procedure;
assigning a user element as a member of a policy binding node, the user element being contained by the corresponding policy class, and the policy binding node delineating at least one policy permission on an object element and granting the policy permission on the object element to the user element; and
evaluating the NGAC graph with the graph evaluation procedure to determine graph analysis information relative to at least one of the user element, the granted policy permission, or the object element based in part on a singular traversal path through the NGAC graph between the user element and the object element via the policy binding node.
|