| CPC H04L 45/02 (2013.01) [H04L 41/12 (2013.01); H04L 45/04 (2013.01); H04L 45/22 (2013.01); H04L 45/28 (2013.01); H04L 45/32 (2013.01); H04L 63/1408 (2013.01)] | 20 Claims |
|
1. A method comprising:
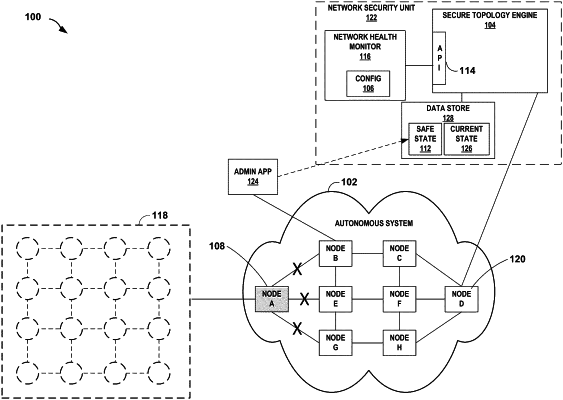
determining, by a computing device comprising one or more processors, safe state data indicative of a physical state of a topology of a computer network comprising a plurality of routing nodes;
detecting, by the computing device, an indicator of a potential network attack; and
in response to detecting the indicator of the potential network attack:
comparing, by the computing device, the safe state data indicative of the physical state of the topology of the computer network with current state data indicative of a running state of the topology of the computer network;
identifying, by the computing device and based on the comparison, a routing node of the plurality of routing nodes as a compromised node; and
reporting, by the computing device, an indication of the compromised node.
|