| CPC G06Q 10/0635 (2013.01) [H04L 63/102 (2013.01); H04L 63/1425 (2013.01)] | 19 Claims |
|
1. A method of detecting and responding to anomalous activity within a system comprising:
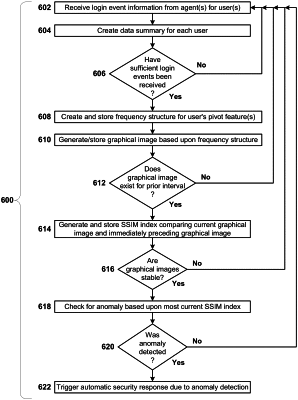
receiving pivot feature information for an aspect of the system at at least one anomaly detection unit, wherein the pivot feature information includes at least one of logins by users, downloads by users on particular machines, or logins on particular machines, and receiving binning feature information representing a periodic temporal interval during each period of which the pivot feature information is expected to be statistically similar;
for a snapshot interval, generating a frequency structure interrelating the pivot feature information, the binning feature information, and counts;
using the frequency structure, generating a two-dimensional graphical image to act as a data structure storing the pivot feature information, wherein the graphical image is of a first specified dimension and a second specified dimension, and wherein the first specified dimension corresponds to the periodic temporal interval, the graphical image having been generated such that a bin of multiple bins, is the bin having a highest count, and the bin is scaled to the specified second dimension, and wherein counts of all other bins in the interval are scaled relative to that highest count;
using an image similarity indexing algorithm to automatically compare the generated graphical image to an immediately preceding graphical image for similarity relative to a pre-specified similarity threshold; and
when a result of the comparison fails to satisfy the pre-specified similarity threshold, automatically preventing a user from communicating using a machine that the user logged in to and thereby generated pivot feature information indicating anomalous usage, by disabling the user's account on that machine, preventing further user downloads on that machine, or requiring a second factor of authentication for further logins, thus preventing a security breach by the user.
|