| CPC G06F 21/79 (2013.01) [G06F 12/1408 (2013.01); G06F 21/606 (2013.01); G06F 21/62 (2013.01); G06F 2221/2107 (2013.01); G06F 2221/2125 (2013.01)] | 18 Claims |
|
1. A data encryption system comprising:
an encryption engine comprising a plurality of encryption cores each configured to perform at least one of an encryption function, a decryption function, or a message authentication function;
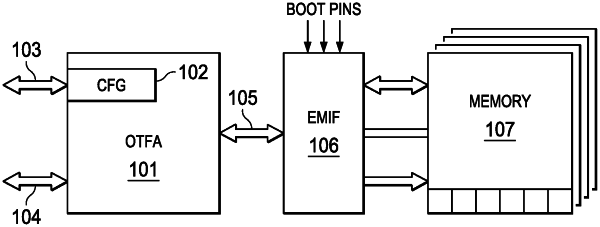
an external memory comprising a set of memory regions that include a first memory region for storing encrypted data and a second memory region for storing unencrypted data; and
an external memory interface configured to write encrypted data received from the encryption cores to the external memory, and further configured to provide encrypted data received from the external memory to the encryption cores;
wherein the encryption engine further comprises circuitry configured to perform a region checking function to:
identify whether a memory write access command attempts to cross a memory region boundary by accessing the first memory region and the second memory region; and
when the memory write access command attempts to cross the memory region boundary:
inhibit execution of the identified memory write access command so that write data corresponding to the identified memory write access command is prevented from being written to any location in the external memory; and
generate an error condition.
|