| CPC G06F 21/755 (2017.08) [G06F 21/57 (2013.01)] | 20 Claims |
|
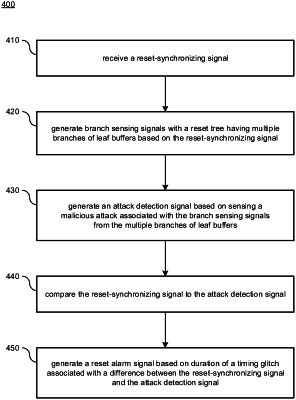
16. A method comprising:
receiving a reset-synchronizing signal;
generating branch sensing signals with a reset tree having multiple branches of the leaf buffers based on the reset-synchronizing signal;
generating an attack detection signal based on sensing a malicious attack associated with the branch sensing signals from the multiple branches of the leaf buffers;
comparing the reset-synchronizing signal to the attack detection signal; and
generating a reset alarm signal based on duration of a timing glitch associated with a difference between the reset-synchronizing signal and the attack detection signal.
|