| CPC G06F 21/64 (2013.01) [G06F 21/566 (2013.01); G06F 2221/2101 (2013.01); G06F 2221/2115 (2013.01)] | 15 Claims |
|
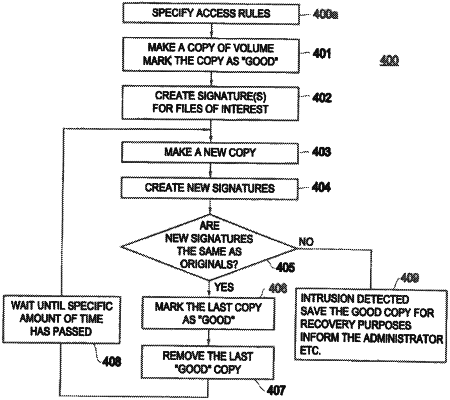
1. An intrusion detection and recovery system, comprising:
creating a space efficient point-in-time copy operation, at time of creation, creating a storage level logical unit of an internal data structure set up that instantaneously creates a copying module that periodically creates a point-in-time copy of the storage level logical unit, said point-in-time copy comprising signatures of said storage level logical unit;
a comparison module that compares at least a portion of said point-in-time copy with a previous copy of the storage level logical unit; and
a judging module that, based on results of said comparison module, judges if a modification has occurred,
wherein a signature of said point-in-time copy is compared with a signature of said previous copy to detect a sign of an intrusion,
further comprising a removing module that, when the intrusion has been judged, removes said point-in-time copy and saves said previous copy of the storage level logical unit for data recovery,
wherein the signatures of said storage level logical unit comprise encoded data of files of said storage level logical unit that are monitored in said point-in-time copy, and
wherein the internal data structure is set up so that reads from data blocks of the storage level logical unit copy are translated to reads from an original storage level logical unit based on the point-in-time copy of the storage level logical unit being created,
further comprising a defining module that defines the access rules to identify the files of said storage level logical unit that are monitored in said point-in-time copy,
wherein the access rules define types of actions including altering and appending data contained in the files of said storage level logical unit that are allowed to be performed on the files of said storage level logical unit and types of actions including altering and appending metadata associated with the files of said storage level logical unit that are to be treated as the intrusion on the files of said storage level logical unit.
|