| CPC G06F 21/6254 (2013.01) [H04L 9/008 (2013.01); H04L 9/3006 (2013.01); H04L 51/52 (2022.05); H04L 51/58 (2022.05)] | 10 Claims |
|
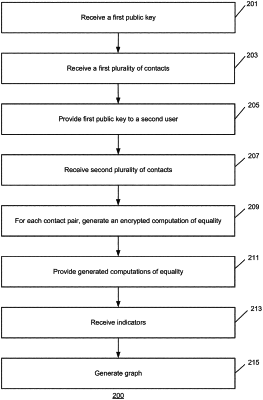
1. A method for graphing relationships in an application while providing anonymity comprising:
receiving, from a first computing device of a first user of a social networking application, a first public key of the first user by a second computing device;
receiving, from the first computing device of the first user of the social networking application, a first plurality of contacts in the social networking application by the second computing device, wherein each contact of the first plurality of contacts is encrypted by the first computing device of the first user using the first public key;
providing the first public key to a third computing device of a second user of the social networking application by the second computing device;
receiving, from the third computing device of the second user, a second plurality of contacts in the social networking application by the second computing device, wherein each contact of the second plurality of contacts is encrypted by the third computing device of the second user using the first public key of the first user;
for each contact pair comprising a contact from the first plurality of contacts and a contact from the second plurality of contacts, generating an encrypted computation of equality for the contact pair using the first public key of the first user by the second computing device; and
providing the generated encrypted computation of equality for each contact pair to the first computing device of the first user by the second computing device.
|