| CPC G06F 21/602 (2013.01) [G06F 9/45558 (2013.01); G06F 11/301 (2013.01); G06F 11/3476 (2013.01); G06F 21/31 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01)] | 19 Claims |
|
1. A method comprising:
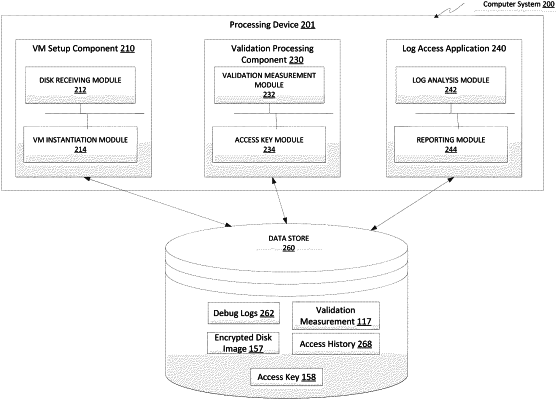
receiving, by a processing device, from a computing device, an encrypted virtual disk image comprising a set of debug logs;
initiating, by the processing device, instantiation of a virtual machine (VM) using the encrypted virtual disk image, wherein the VM is to execute a log access application to analyze the set of debug logs;
sending, to the computing device, by the processing device, a validation measurement and a first request for access to a first type of data associated with the set of debug logs by the log access application, wherein the validation measurement comprises a cryptographic signature indicating that the VM is executing the log access application; and
receiving, from the computing device, a first indication granting access to a first portion of the set of debug logs by the log access application, wherein the first portion of the set of debug logs represents the first type of data, and wherein having access to the first portion of the set of debug logs allows the log access application to analyze the first portion of the set of debug logs to identify a first issue associated with the first type of data associated with the set of debug logs.
|