| CPC G06F 21/577 (2013.01) [G06F 21/552 (2013.01); G06F 21/554 (2013.01); G06F 21/562 (2013.01); G06F 21/566 (2013.01); G06F 21/568 (2013.01)] | 20 Claims |
|
1. A non-transitory computer readable medium having stored thereon instructions comprising executable code which when executed by one or more processors, causes the processors to:
receive cloud-element data related to a cloud-based element in a cloud environment;
receive first vulnerability data from a first vulnerability source;
receive second vulnerability data from a second vulnerability source that is a vendor of a particular operating system;
receive cloud-element context data comprising the particular operating system of the cloud-based element from the cloud environment;
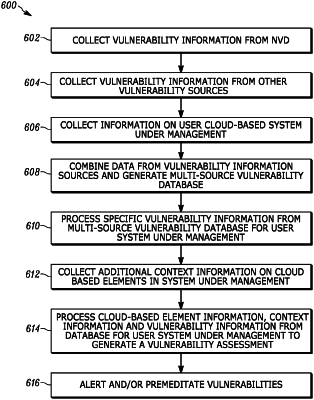
replace the first vulnerability source and the second vulnerability source with a multiple-source vulnerability database generated from both the first vulnerability data and from the second vulnerability data such that a reported vulnerability from the first vulnerability source and a separate reported vulnerability from the second vulnerability source are combined into a single common vulnerability in the multiple-source vulnerability database;
evaluate the cloud-element data and the cloud-element context data using the multiple-source vulnerability database to generate a vulnerability assessment related to the single common vulnerability and the particular operating system; and
generate a list of remediation steps in response to the vulnerability assessment.
|