| CPC G06F 21/577 (2013.01) [G06F 2221/033 (2013.01)] | 20 Claims |
|
1. A system, comprising:
one or more processors;
one or more computer-readable non-transitory storage media comprising instructions that, when executed by the one or more processors, cause one or more components of the system to perform operations comprising:
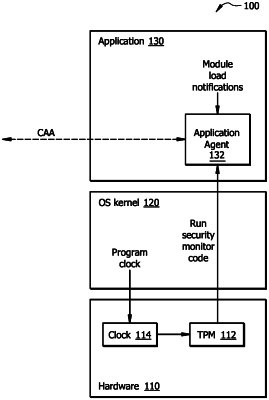
receiving, at an application agent, a load map associated with an application, the load map indicating loaded modules of the application, the load map being a dynamic software bill of material (SBOM);
determining whether at least one notification is received indicating at least one update to the loaded modules of the application,
wherein, when the at least one notification is received, the load map is updated based on the indicated at least one update, and
wherein, when the at least one notification is not received, the load map is retained in an existing state;
periodically retrieving one or more call traces associated with the application, the one or more call traces indicating executed modules of the application; and
generating a continuous application attestation comprising at least a combination of the updated load map or the retained load map, and the retrieved one or more call traces associated with the application at a given time.
|