| CPC H04W 12/06 (2013.01) [G06F 9/547 (2013.01); G06F 21/6218 (2013.01)] | 22 Claims |
|
1. A system comprising:
one or more processors;
a data storage device; and
a computer-readable storage device storing instructions which, when executed by the one or more processors, cause the one or more processors to perform operations comprising:
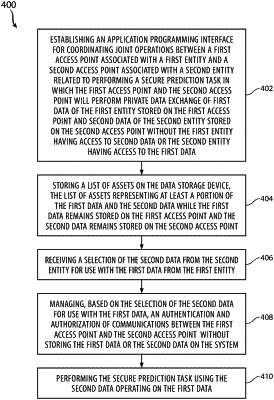
establishing an application programming interface for coordinating joint operations between a first access point associated with a first entity and a second access point associated with a second entity, wherein the joint operations are related to performing a secure prediction task in which the first access point and the second access point will perform private computation of first data of the first entity stored on the first access point and second data of the second entity stored on the second access point without the first entity having access to second data or the second entity having access to the first data;
storing a list of assets on the data storage device, the list of assets representing metadata about the first data and the second data while the first data remains stored on the first access point and the second data remains stored on the second access point;
receiving a selection of the second data from the second entity for use with the first data from the first entity;
managing, based on the selection of the second data for use with the first data, an authentication and authorization of communications between the first access point and the second access point without storing the first data or the second data on the system; and
performing the secure prediction task using the second data operating on the first data.
|