| CPC H04L 63/20 (2013.01) | 20 Claims |
|
1. A method, comprising:
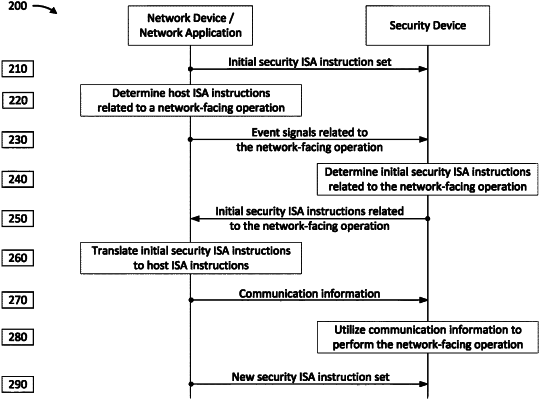
transmitting, by a network device to a security device, an initial security instruction set including a plurality of initial security machine code instructions to be executed by a security operating system associated with the security device, the plurality of initial security machine code instructions being determined based at least in part on associating each of the plurality of initial security machine code instructions with respective sets of random numbers;
transmitting, by the network device to the security device, an event signal identifying a network-facing operation that is to be executed by the network device and carried out by the security device over a network;
receiving, by the network device from the security device based at least in part on transmitting the event signal, a security machine code instruction associated with the security device carrying out the network-facing operation, the security machine code instruction being selected from among the plurality of initial security machine code instructions based at least in part on the identified network-facing operation;
translating, by the network device, the security machine code instruction into a host machine code instruction to be executed by a network operating system associated with the network device;
transmitting, by the network device to the security device based at least in part on executing the translated host machine code instruction, communication information to enable the security device to carry out the network-facing operation;
determining, by the network device, a new security instruction set including a plurality of new security machine code instructions to be executed by the security operating system associated with the security device, and
transmitting, by the network device to the security device, the new security instruction set to the security device.
|