| CPC H04L 63/20 (2013.01) [G06F 16/2477 (2019.01); G06F 16/951 (2019.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01)] | 16 Claims |
|
1. A system for automated cybersecurity defensive strategy analysis and recommendations, comprising:
an attack implementation engine comprising a first plurality of programming instructions stored in a memory of, and operating on a processor of, a computing device, wherein the first plurality of programming instructions, when operating on the processor, cause the computing device to:
execute a cyberattack on a network under test; and
gather system information about the operation of the network under test during the cyberattack, the system information comprising information about the sequence of events and response of affected devices during the cyberattack;
a machine learning simulator comprising a second plurality of programming instructions stored in the memory of, and operating on the processor of, the computing device, wherein the second plurality of programming instructions, when operating on the processor, cause the computing device to:
use the system information to initiate an iterative simulation of a cyberattack strategy sequence, each iteration comprising a simulated attack on a model of the network under test and a simulated defense against the simulated attack, each simulated attack being generated by a first machine learning algorithm;
obtain a simulation result comprising the cyberattack strategy sequence and a probability of success of the attack and the defense in each iteration; and
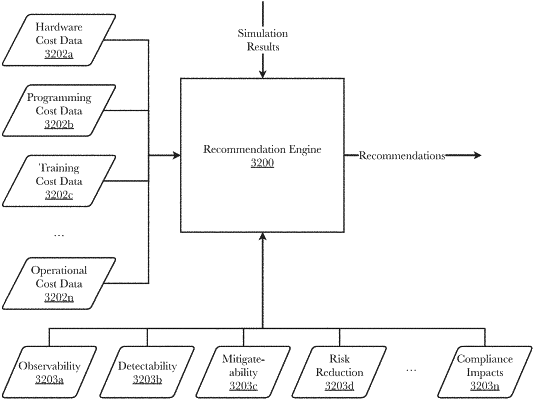
a recommendation engine comprising a third plurality of programming instructions stored in the memory of, and operating on the processor of, the computing device, wherein the third plurality of programming instructions, when operating on the processor, cause the computing device to:
compare the simulation result against one or more cost factors and one or more benefit factors; and
determine a cybersecurity improvement recommendation for the network under test based on the comparison.
|