| CPC H04L 63/20 (2013.01) [G06F 9/5027 (2013.01); H04L 63/02 (2013.01); H04L 63/1408 (2013.01)] | 20 Claims |
|
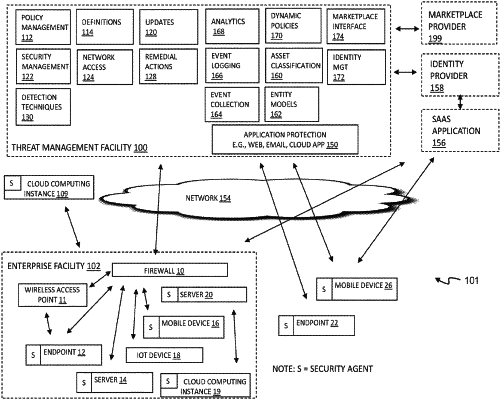
1. A computer-implemented method comprising:
receiving, by a network device configured to perform a plurality of security tasks, from an endpoint device coupled to the network device via a network, tag information about traffic flow from the endpoint device to the network device over the network, wherein the tag information includes one or more characteristics of the traffic flow;
identifying, by the network device, a subset of the plurality of security tasks to be performed by the network device for the traffic flow, based at least in part on the tag information, wherein the subset excludes at least one security task of the plurality of security tasks;
sending, from the network device to the endpoint device, an indication of the at least one security task that is excluded from the subset and that is to be performed for the traffic flow at the endpoint device prior to the endpoint device sending the traffic flow to the network device;
after sending the indication, receiving the traffic flow by the network device from the endpoint device; and
performing for the traffic flow, by the network device, each task in the subset of the plurality of security tasks.
|