| CPC H04L 63/1483 (2013.01) [G06F 16/2282 (2019.01); G06F 16/245 (2019.01); H04L 51/48 (2022.05); H04L 63/083 (2013.01); H04L 63/0876 (2013.01); H04L 63/306 (2013.01); H04L 2463/082 (2013.01)] | 17 Claims |
|
1. A system for identifying email messages associated with phishing threats comprising:
a memory configured to store a token-email address mapping table comprising a plurality of email addresses mapped to a plurality of tokens, wherein:
each of the plurality of email addresses is associated with a different token from the plurality of tokens, and
each of the plurality of tokens uniquely identifies a different email address from the plurality of email addresses; and
a hardware processor, operably coupled with the memory, and configured to:
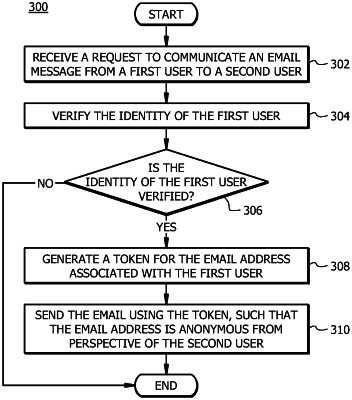
access an email message sent to a receiving computing device associated with a receiver of the email message, wherein the email message is associated with a sender's email address;
determine whether the sender's email address is associated with a token from the plurality of tokens by searching for the sender's email address within the token-email address mapping table;
in response to determining that the sender's email address is not associated with a token from the plurality of tokens, determine that the email message is associated with a phishing threat;
generate the token-email address mapping table by:
receiving a request from a sending computing device associated with the sender to send the email message;
verifying the identity of the sender by performing a first multi-factor authentication;
in response to verifying the identity of the sender, generating the token uniquely identifying the sender's email address;
associating the sender's email address with the token; and
storing the sender's email address linked to the token in the token-email address mapping table, wherein the token is used once, such that after receipt of the email message the token is erased.
|