| CPC H04L 63/1433 (2013.01) [G06F 9/44505 (2013.01); G06F 9/541 (2013.01); G06F 9/547 (2013.01); G06F 16/951 (2019.01); H04L 63/1466 (2013.01); H04L 67/133 (2022.05)] | 20 Claims |
|
1. A method for securing an application programing interface (API) against a vulnerability, the method comprising:
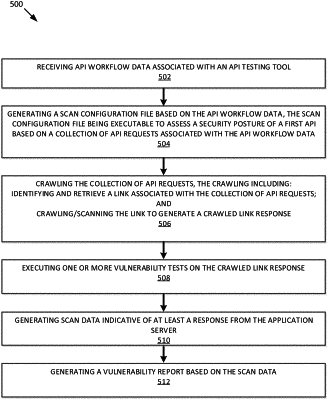
receiving, using one or more computing devices processors, API workflow data associated with an API testing tool;
generating, using the one or more computing device processors, a scan configuration file based on the API workflow data, the scan configuration file being executable to assess a security posture of a first API based on a collection of API requests associated with the API workflow data;
determining, using the one or more computing device processors, at least one endpoint associated with the collection of API requests;
determining, using the one or more computing device processors, that the at least one endpoint accesses a resource of an application server via the first API;
crawling, using the one or more computing device processors, the collection of API requests, the collection of API requests including one or more parameters providing or comprising one or more options that are passable to the application server via the collection of API requests, the one or more options including at least one of a POST command, a GET command, a PUT command, and a DELETE command;
executing, using the one or more computing device processors, one or more vulnerability tests on the one or more parameters, the executing comprising:
determining API data for the collection of API requests,
scanning the one or more parameters based on the API data,
generating, using the one or more computing device processors, scan data indicative of at least one vulnerability associated with the first API based on the scanning; and
generating, using the one or more computing device processors, a vulnerability report based on the scan data.
|