| CPC H04L 63/1425 (2013.01) [G06F 9/45558 (2013.01); H04L 41/22 (2013.01); H04L 43/06 (2013.01); G06F 2009/45591 (2013.01); H04L 63/168 (2013.01)] | 20 Claims |
|
1. A method, comprising:
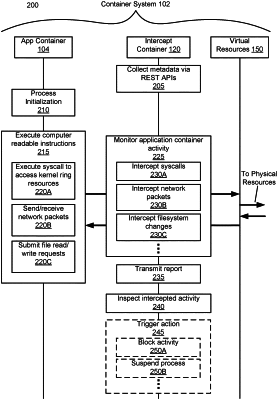
monitoring one or more activities of an application container in a container system by intercepting data from the one or more activities of the application container, the application container including computer-readable instructions and initiated via a container service and isolated using operating system-level virtualization that is enabled by a kernel of an operating system, the kernel enabling a plurality of containers sharing the kernel, the plurality of containers including the application container and an intercept container, the monitoring performed by the intercept container using the kernel to access the application container, wherein monitoring the one or more activities comprises:
intercepting, by the intercept container, a network activity of the application container attempting to transmit a file to a network destination outside of the container system, wherein content of the file is encapsulated outside of the application container such that the content is obfuscated outside of the application container; and
obtaining, by the intercept container using the kernel to access the application container, an encryption key from a process monitor of the intercept container which retrieves the encryption key by a scan inspection of a memory of the application container, and wherein the encryption key is used to access an unobfuscated content of the file that corresponds to the network activity prior to the file being obfuscated and transmitted out of the application container;
inspecting the content of the file being attempted to be transmitted to the network destination associated with the network activity, wherein inspecting the content of the file comprises: retrieving a template corresponding to a policy that controls transmission of sensitive personal data, the template comprising one or more regular expressions that represent patterns of the sensitive personal data;
applying, by the intercept container, the one or more regular expressions to the unobfuscated content of the file that is obtained using the kernel to find whether one or more regular expression matches exist in the content of the file;
determining, in response to one or more regular expression matches are found, that the network activity attempting to transmit the file to the network destination involves an attempt to transmit the sensitive personal data out of the application container; and
triggering an action specified in the policy in response to determining that the network activity involves the attempt to transmit the sensitive personal data out of the application container.
|