| CPC H04L 63/1416 (2013.01) [G06N 20/00 (2019.01)] | 20 Claims |
|
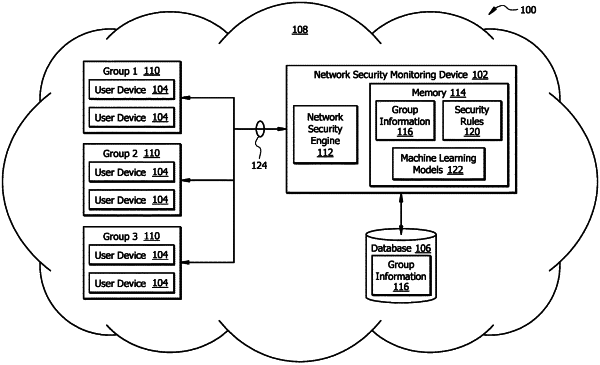
1. A network security device, comprising:
a network interface in signal communication with a plurality of user devices; and
a processor in signal communication with the network interface, and configured to:
obtain a first user interaction data at a first time instance for the plurality of user devices, wherein the first user interaction data identifies activities performed by the plurality of user devices before the first time instance;
input the first user interaction data into a machine learning model, wherein the machine learning model is configured to output a first set of clusters for the plurality of user devices based on the first user interaction data;
determine a first cluster quantity that identifies a number of clusters within the first set of clusters;
obtain a second user interaction data at a second time instance for the plurality of user devices, wherein the second user interaction data identifies activities performed by the plurality of user devices between the first time instance and the second time instance;
input the second user interaction data into the machine learning model, wherein the machine learning model is configured to output a second set of clusters for the plurality of user devices based on the second user interaction data;
determine a second cluster quantity that identifies a number of clusters within the second set of clusters;
compare the first cluster quantity to the second cluster quantity;
determine the second cluster quantity is greater than the first cluster quantity;
identify a first cluster from the second set of clusters that is not present in the first set of clusters;
identify a first user device within the first cluster; and
modify one or more device settings on the first user device.
|