| CPC H04L 63/08 (2013.01) | 20 Claims |
|
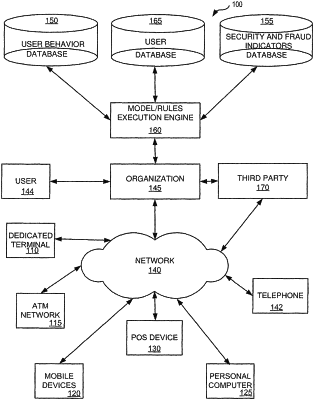
1. A method comprising:
receiving, from a user device, an activity request from a user;
ranking authentication methods according to a level of invasiveness for the activity request, wherein the ranking assigns rank values, for each particular authentication method, according to a level of user-provided information the particular authentication method requires and a level of passive information provided by the user device for the particular authentication method; and
generating an authentication plan that includes an authentication method, wherein the authentication plan:
compares an identity trust score to an activity trust threshold for the activity request; and
selects the authentication method, in part, according to the level of invasiveness rankings such that authentication methods with higher levels of passive information provided by the user device are prioritized higher than authentication methods with higher levels of user-provided information.
|