| CPC H04L 9/3213 (2013.01) [H04L 9/3271 (2013.01); H04L 63/0815 (2013.01); H04L 63/10 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01); H04W 12/06 (2013.01)] | 42 Claims |
|
1. A system, comprising:
a network interface; and
one or more processors, configured to cooperatively perform a process that includes:
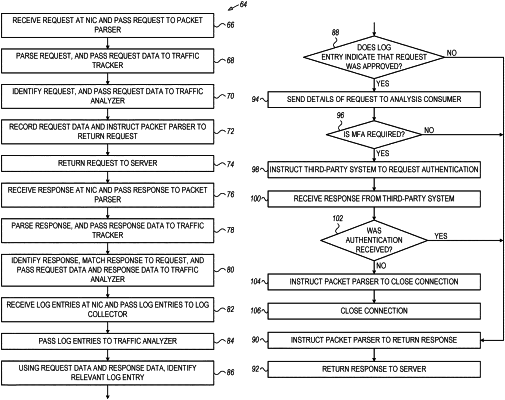
receiving, via the network interface, a request originating from a request- origin application and directed to a request-destination application that runs on a request-destination device,
subsequently to receiving the request, communicating the request to the request-destination device,
subsequently to communicating the request to the request-destination device, matching the request to at least one log entry of multiple log entries recorded by the request-destination application by identifying that the log entry was recorded responsively to the request, and receiving a response, from the request-destination application, to the request,
while holding the response, identifying, in the at least one log entry, information associated with the request or with the response, and
performing a function in response to the information and in accordance with a security rule.
|