| CPC H04L 9/0869 (2013.01) [H04L 9/3093 (2013.01); H04L 9/3247 (2013.01)] | 6 Claims |
|
1. A method for forming a virtual private network performed by a server including a processor, the method comprising the steps of:
generating, by the processor, a private key including a first key vector generated by a lattice-based algorithm, a second key vector having a first distance from the first key vector, and a key matrix corresponding to a random polynomial ring;
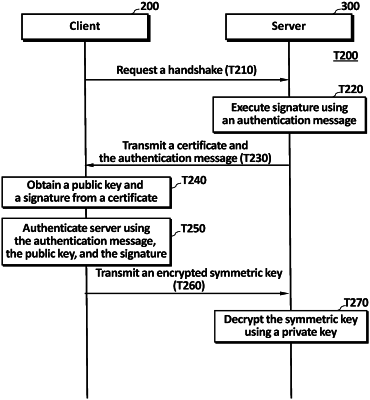
receiving, by the processor, a handshake request from a client;
performing, by the processor, a signature using the private key;
transmitting, by the processor, a certificate and an authentication message including the signature to the client;
determining, by the processor, whether a signature value is equal to or less than a predetermined value; and
transmitting, by the processor, the certificate and the authentication message to the client only when the signature value is equal to or less than the predetermined value,
wherein the performing of the signature includes:
obtaining, by the processor, a first bit based on the key matrix;
obtaining, by the processor, a first hash value for the first bit and the authentication message; and
generating, by the processor, the signature value using the first hash value and the first key vector,
wherein the obtaining the first bit based on the key matrix includes:
obtaining, by the processor, a signature random number by using a random number generator;
calculating, by the processor, a first matrix by multiplying the key matrix by the signature random number; and
obtaining, by the processor, upper N (N is a natural number) coefficients of a polynomial ring corresponding to the first matrix as the first bit,
wherein the generating of the signature value by using the first hash value and the first key vector comprises calculating, by the processor, the signature value by adding the signature random number to a value obtained by multiplying the first hash value and the first key vector.
|