| CPC G06F 21/6218 (2013.01) [G06F 9/54 (2013.01); G06F 16/1748 (2019.01)] | 14 Claims |
|
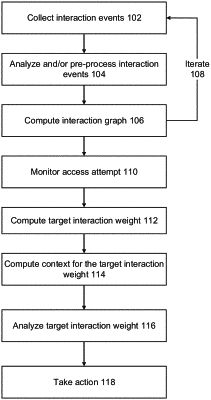
1. A computer implemented method for securing at least one of files and records, the method comprising:
creating an interaction graph defining interaction events between users and at least one of files and records and between users;
monitoring an attempt by a target user to access at least one of a target file and a target record;
computing a target interaction weight represents contribution interaction weights between the target user and other users that contributed to the at least one of the target file and the target record;
adjusting the contribution interaction weights according to a decay parameter computed as a function of time elapsing from the contributions to the file and the interaction events between the target user and the other users that contributed to the at least one of the target file and the target record;
adjusting the contribution interaction weights according to a decay parameter computed as a function of time elapsing from the contributions to the file to the attempt to access the file;
computing the target interaction weight by summing the contribution interaction weights between the target user and the other users that contributed to the at least one of the target file and the target record;
comparing a target threshold with the target interaction weight; and
in response to the comparison satisfying a rule, at least one of:
(i) raising or filtering a security alert that corresponds to the target user and to at least one of the target file and the target record, and
(ii) blocking access by the target user to the at least one of the target file and the target record.
|