| CPC G06F 21/577 (2013.01) [G06F 16/285 (2019.01); G06F 21/604 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A method comprising:
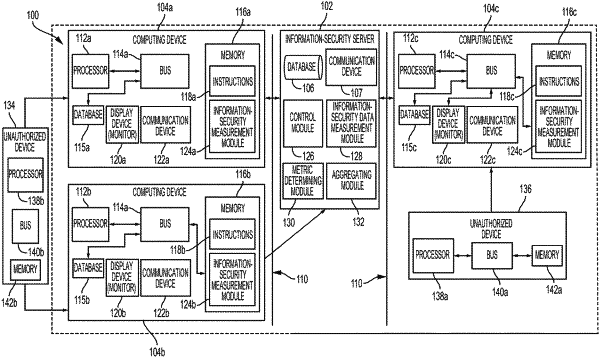
receiving, by a processing device, information-security data that indicates information-security activity detected in a computing environment by one or more information-security measurement modules;
determining, by the processing device, a plurality of information-security metrics based on the information-security data; and
generating, by the processing device, an interactive user interface for display that includes the plurality of information-security metrics categorized into one or more groups, the interactive user interface being usable by a user for improving a security level of the computing environment.
|