| CPC G06F 21/564 (2013.01) [G06N 20/00 (2019.01)] | 16 Claims |
|
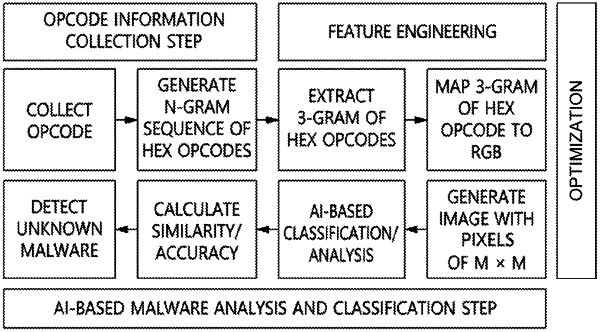
1. A method for detecting unknown malware, comprising:
collecting operation code (opcode) information from a detection target;
generating a multi-pixel image having a variable length by performing feature engineering on the opcode information; and
detecting unknown malware by inputting the multi-pixel image to a deep-learning model based on AI,
wherein the multi-pixel image corresponds to a multi-pixel RGB image based on an n-gram corresponding to the opcode information, and
wherein generating the multi-pixel image comprises:
storing n-gram sequences for hexadecimal (hex) codes having a variable length based on the opcode information; and
mapping a 3-gram of opcodes to an RGB code based on the n-gram sequences, thereby generating the multi-pixel RGB image.
|