| CPC G06F 21/54 (2013.01) [G06F 21/566 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
1. A system for code detection, the system comprising:
one or more computer readable storage devices configured to store a plurality of computer executable instructions; and
one or more hardware computer processors in communication with the one or more computer readable storage devices and configured to execute the plurality of computer executable instructions in order to cause the system to:
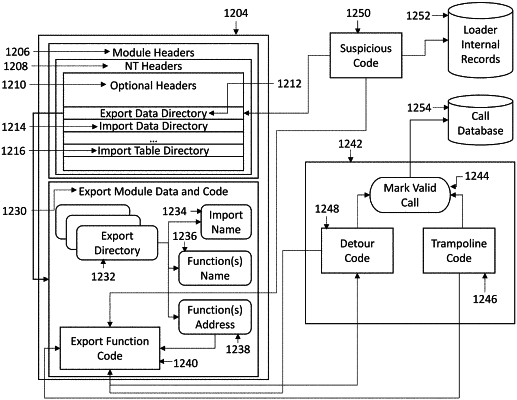
instrument an import address table (IAT) entry of a monitored symbol, the instrumenting of the TAT entry comprising:
replacing a monitored symbol address within the TAT entry of the monitored symbol with a modified address;
executing a first code upon a call of the modified address to detect and validate a call of the monitored symbol; and
redirecting the call of the modified address to the monitored symbol address;
instrument one or more functions, the instrumenting of the one or more functions comprising:
modifying the one or more functions to return values that lead to the code;
detouring execution of the monitored symbol to a second code to detect and validate a call of the monitored symbol; and
redirecting the call of the monitored symbol to the monitored symbol address;
monitor the first code and the second code of the monitored symbol to determine if calls from an executable comprise a static call, a dynamic call, or a local call, wherein determination of whether the calls from the executable comprise a local call comprises monitoring the second code to determine if a return address is located in the same executable as the monitored symbol; and
if the system determines that at least one call from the executable does not comprise a static call, dynamic call, or a local call, flag the executable as suspicious or malicious.
|