| CPC G06F 21/45 (2013.01) [G06N 20/00 (2019.01); G06Q 20/4016 (2013.01); G06F 2221/2103 (2013.01)] | 18 Claims |
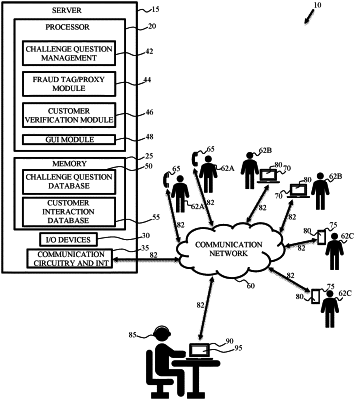
|
1. A method, comprising:
receiving, by a processor, a set of challenge questions for authenticating a plurality of customers to perform high-risk activities in their respective accounts associated with an entity;
wherein the set of challenge questions are based on prior account activities performed by the plurality of customers in their respective accounts;
utilizing, by the processor, at least one machine learning model to determine an authentication score for each challenge question in the set of challenge questions;
wherein the authentication score of each respective challenge question is based on:
i) a first number of instances of a plurality of customer interactions with the entity that a correct answer to a respective challenge question in the set of challenge questions has been given by the plurality of customers of the entity, or
ii) a second number of instances of the plurality of customer interactions with the entity that the correct answer to the respective challenge question in the set of challenge questions has been given by at least one fraudulent person;
ranking, by the processor, challenge questions of the set of challenge questions based on the authentication score;
receiving, by the processor, an electronic request on a computing device from an unverified customer who desires to perform at least one high-risk account activity;
authenticating, by the processor, that the unverified customer is a fraudster when assessing the electronic request from the unverified customer was communicated through an IP address or a telephone number previously associated with fraudulent activity;
authenticating, by the processor, that the unverified customer is a fraudster when assessing answers to the ranked challenge questions presented to the unverified customer are incorrect;
authenticating, by the processor, the unverified customer to form a verified customer when answers to the ranked challenge questions presented to the unverified customer are correct; and
performing by the processor:
allowing the verified customer from the plurality of customers to perform the at least one high-risk account activity with a respective account associated with the verified customer; and
blocking the fraudster to perform the at least one high-risk account activity.
|