| CPC G06F 21/121 (2013.01) [H04L 9/0825 (2013.01); H04L 9/302 (2013.01); H04L 9/3247 (2013.01); G06F 8/60 (2013.01); G06F 21/1063 (2023.08)] | 20 Claims |
|
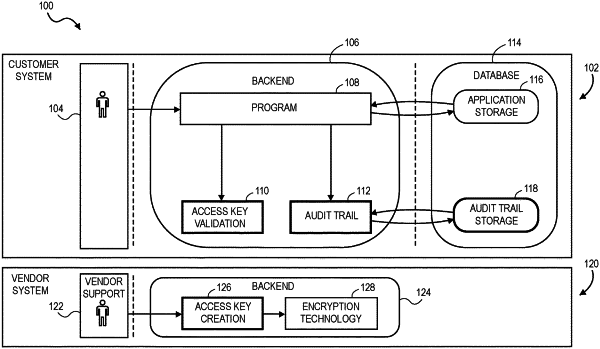
1. A method comprising:
deploying, from a vendor system to a customer system, a first computer program;
receiving, from the customer system, an indication of an inconsistency in a data table encountered during execution of the first computer program;
accessing a second computer program designed to fix the inconsistency;
defining at least one vendor access parameter for the second computer program;
deploying from the vendor system to the customer system, the second computer program;
receiving, from a customer at the customer system, an access key requesting access to execute the second computer program,
wherein the access key comprises a digital signature and at least one customer access parameter;
validating, at the customer system, the digital signature using a public key private key pair,
wherein the private key of the public key private key pair is known by the vendor system as corresponding to one or more vendor-approved users having requisite knowledge to correctly execute the second program to fix the inconsistency;
verifying that the at least one customer access parameter matches the at least one vendor access parameter; and
in response to the verifying, causing execution of the second computer program on the customer system.
|