| CPC G06F 11/321 (2013.01) [G06F 9/45558 (2013.01); G06F 11/3457 (2013.01); G06F 21/577 (2013.01); G06F 2009/4557 (2013.01); G06F 2009/45587 (2013.01)] | 18 Claims |
|
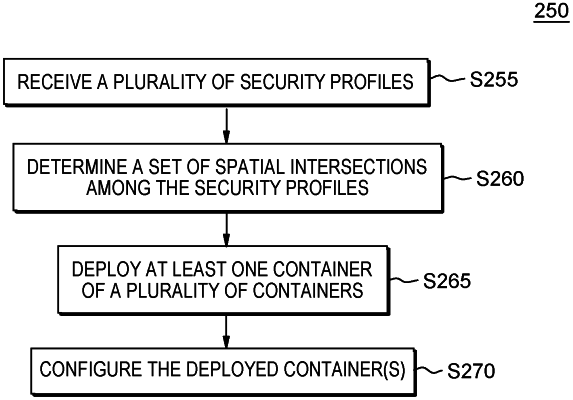
1. A computer-implemented method (CIM) comprising:
receiving, from a security profile library and to a visualization engine, a plurality of security profiles, with each security profile of the plurality of security profiles being represented as a three-dimensional (3D) visual diagram;
determining a set of spatial intersections amongst the plurality of security profiles;
deploying a plurality of containers in the set of spatial intersections, with at least one container of the plurality of containers being deployed in at least one of the spatial intersections; and
responsive to the deployment of the plurality of containers in the set of spatial intersections, configuring the at least one container being deployed with the security profiles corresponding to the at least one spatial intersection.
|