| CPC G06F 9/4406 (2013.01) [G06F 9/30007 (2013.01); G06F 9/52 (2013.01); G06F 16/907 (2019.01); G06N 20/00 (2019.01); G06F 9/4401 (2013.01)] | 24 Claims |
|
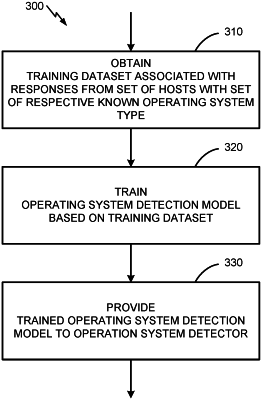
1. A method of training an operating system (OS) detector, the method comprising:
obtaining a training dataset that is associated with responses from a set of training hosts with a set of respective known OS types;
training an OS detection model based on the training dataset; and
providing the trained OS detection model to the OS detector,
wherein the training dataset comprises one or more response-to-OS maps, each response-to-OS map comprising a response metadata of a training host of the set of training hosts and an OS of that training host mapped to that response metadata, each response metadata comprising a pattern of responses from the training host to a probe sequence sent to the training host, the probe sequence comprising a sequence of one or more transport layer probes, and
wherein the trained OS detection model enables the OS detector to detect an OS of a target host based on a response set from the target host to a corresponding probe set sent to the target host, the response set comprising one or more responses, and the probe set comprising one or more transport layer probes.
|