| CPC H04L 63/20 (2013.01) [H04L 63/083 (2013.01); H04L 63/102 (2013.01); H04L 63/105 (2013.01); H04L 63/123 (2013.01)] | 20 Claims |
|
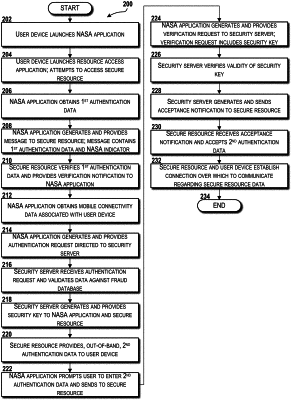
1. A method comprising:
obtaining, by a user device comprising a processor executing a network-assisted secure access application, first authentication data associated with a user who is attempting to access, via the user device, a secure resource;
generating, by the user device, a message directed to the secure resource, wherein the message comprises the first authentication data and an indicator to notify the secure resource that a network-assisted secure access service will be used to assist in providing the user device secure access to the secure resource, and wherein the secure resource verifies the first authentication data;
providing, by the user device, the message to the secure resource;
receiving, by the user device, from the secure resource, a notification that the first authentication data has been verified by the secure resource;
obtaining, by the user device, mobile connectivity data associated with the user device;
generating, by the user device, an authentication request directed to a security server, wherein the authentication request comprises the mobile connectivity data to be verified by the security server;
providing, by the user device, the authentication request to the security server that validates the mobile connectivity data against a fraud database;
receiving, by the user device, from the security server, a security key, wherein receipt of the security key indicates that the security server has validated the mobile connectivity data against the fraud database, and wherein the security server also provides the security key to the secure resource;
prompting, by the user device, the user to input second authentication data;
providing, by the user device, the second authentication data to the secure resource;
generating, by the user device, a verification request comprising the security key; and
providing, by the user device, the verification request to the security server, wherein the security server verifies that the security key is valid and provides an acceptance notification to the secure resource to notify the secure resource to accept the second authentication data and grant the user device access to the secure resource.
|