| CPC H04L 63/1466 (2013.01) [H04L 12/4641 (2013.01); H04L 63/1416 (2013.01)] | 25 Claims |
|
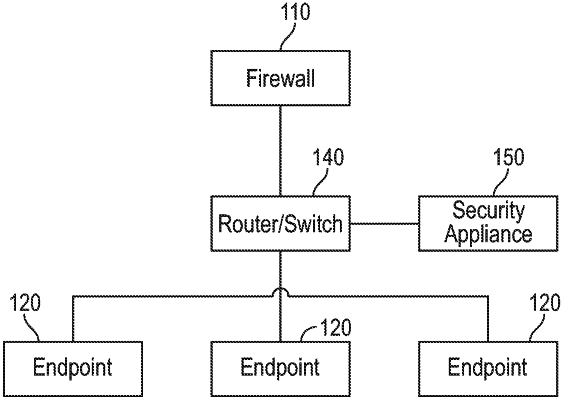
1. A method of preventing propagation of ransomware, comprising:
monitoring, by an extension to a web browser installed on an endpoint device, inbound connection requests to the endpoint device, the monitoring including monitoring for protocols vulnerable to ransomware attack; and
in response to detecting a vulnerable protocol, the extension of the web browser selecting, from a plurality of certificates for different ransomware threat levels, a certificate corresponding to a heightened ransomware risk level;
the extension to web browser providing the selected certificate to an identity provider during single-sign on authentication.
|