| CPC H04L 63/1441 (2013.01) [G06F 16/285 (2019.01); G06F 21/554 (2013.01); H04L 63/0236 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/20 (2013.01); H04L 47/2425 (2013.01)] | 20 Claims |
|
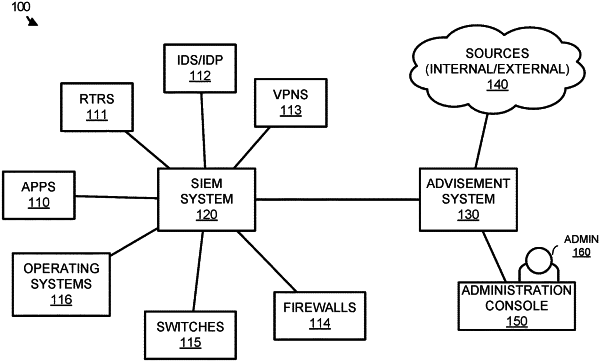
1. A computer-implemented method performed by an advisement system coupled to a computing environment, the computing environment comprising a plurality of computing assets, the method comprising:
identifying a security threat involving the computing environment;
obtaining state information for the security threat;
determining, based on the state information, that the security threat comprises a malicious process in a reconnaissance state in which the malicious process is attempting to gather information about a structure of the computing environment;
identifying a security action for responding to the security threat based on determining that the security threat comprises a malicious process in a reconnaissance state in which the malicious process is attempting to gather information about a structure of the computing environment;
translating the security action into a process to be implemented at a computing asset of the plurality of computing assets; and
initiating implementation of the security action at the computing asset of the plurality of computing assets.
|