| CPC H04L 63/1416 (2013.01) [G06N 20/00 (2019.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); H04L 63/164 (2013.01)] | 18 Claims |
|
1. An artificial intelligence (“AI”) method for unifying cyberthreats detected by disparate software tools deployed across an enterprise organization, the AI method comprising:
inventorying a first set of technical attributes that define a first device;
based on the first set of technical attributes, generating a set of model technical attributes;
searching for a second device that includes a second set of technical attributes that maps onto the set of model technical attributes;
detecting a first vendor tool operating on the first device;
detecting a second vendor tool operating on the second device;
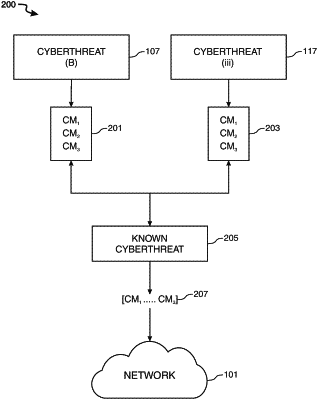
diverting computing resources to identify duplicate cyberthreats detected by the first and second vendor tools;
identifying the duplicate cyberthreats by determining there are more than a threshold number of countermeasures output by the first vendor tool which overlap countermeasures output by the second vendor tool; and
upon a determination that the second set of technical attributes maps onto the set of model technical attributes based on fuzzifying the second set of technical attributes decommissioning the second vendor tool and applying the first vendor tool to both the first and second devices.
|