| CPC H04L 63/1416 (2013.01) [G06N 7/01 (2023.01); G06N 20/00 (2019.01); H04L 12/40 (2013.01); B60R 16/023 (2013.01); H04L 2012/40215 (2013.01)] | 11 Claims |
|
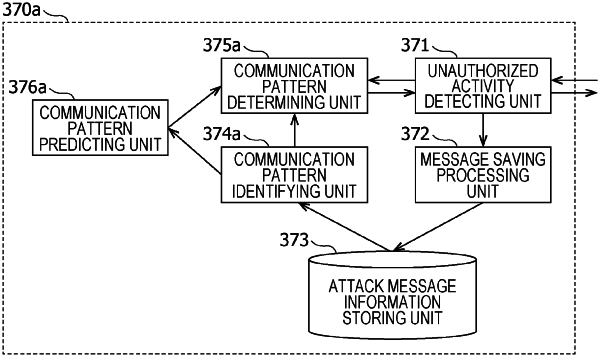
1. A reference message determining method used in unauthorized communication detection in an onboard network system that is executed by an information processing system including at least one memory, the onboard network system including a network and one or more electronic control units connected to the network, the reference message determining method comprising:
identifying, from information relating to an attack message on the onboard network system detected in the unauthorized communication detection, a communication pattern indicating features of the attack message;
determining whether or not at least two messages sent out onto the network during a predetermined reception cycle match the communication pattern identified in the identifying; and
determining that one of the at least two messages determined not to match the communication pattern is to be used as a reference message for detecting the unauthorized communication during a predetermined next reception cycle, the reference message being used for calculation of data values or a reception time of a message to be received in the next reception cycle.
|