| CPC H04L 63/101 (2013.01) [H04L 43/50 (2013.01); H04L 63/0263 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
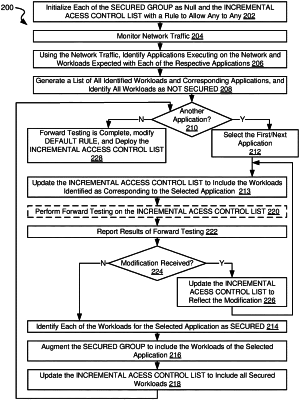
1. A method for performing forward testing on an access control list in a network environment, the method comprising:
accessing, by a processing resource, a first access control list including at least a first workload rule that allows a first type of network communication and a default rule, wherein the first type of network communication corresponds to a first application;
modifying, by the processing resource, the first access control list to yield a second access control list, wherein the second access control list additionally includes at least a secure rule and a second workload rule other than the first workload rule, wherein the secure rule blocks at least the first type of network communication, wherein the second workload rule allows a second type of network communication, and wherein the second type of network communication, different from the first type of network communication, corresponds to the second application; and
forward testing, by the processing resource, the second access control list, wherein the forward testing includes applying a set of network control rules included in the second access control list in a sequence until one of the rules in the set of network control rules is satisfied, and wherein the sequence as applied to the network control rules is based on an order list that includes:
applying first the first workload rule before the secure rule;
applying the secure rule before applying the second workload rule;
applying the second workload rule before applying the default rule; and then
applying the default rule.
|