| CPC H04L 63/101 (2013.01) [G06F 21/62 (2013.01); H04L 41/0627 (2013.01); H04L 41/22 (2013.01); H04L 63/0435 (2013.01); H04L 63/10 (2013.01); H04L 63/105 (2013.01); H04L 63/20 (2013.01); G06F 16/9024 (2019.01)] | 20 Claims |
|
1. A system, comprising:
an access control analyzer comprising one or more processors and one or more memories to store computer-executable instructions that, when executed, cause the one or more processors to:
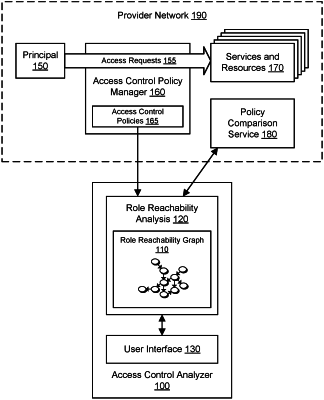
determine a first node in a graph, wherein the first node corresponds to a first role in a provider network hosting a plurality of services and resources, wherein the first role is associated with a first access control policy, and wherein the first access control policy grants or denies access to a first one of the services and resources;
determine a second node in the graph, wherein the second node corresponds to a second role in the provider network, wherein the second role is associated with a second access control policy, and wherein the second access control policy grants or denies access to a second one of the services and resources;
perform a role reachability analysis that determines whether the first role can assume the second role for a particular state of one or more key-value tags, wherein one or more role assumption steps provide temporary access during a role session, wherein the role reachability analysis determines a third access control policy authorizing a complement of a role assumption request for the second role, wherein the role reachability analysis determines whether the first role can assume the second role based at least in part on an analysis of the third access control policy with respect to a role assumption policy for the second role for the particular state of the one or more key-value tags, and wherein the role assumption request is not authorized when the third access control policy does include the role assumption policy for the second role for the particular state of the one or more key-value tags; and
based at least in part on the role reachability analysis, grant or deny access to the second one of the services and resources to a principal in the first role.
|