| CPC H04L 63/0876 (2013.01) [H04L 63/107 (2013.01); H04L 63/1408 (2013.01); H04W 12/06 (2013.01); H04W 12/12 (2013.01); H04W 12/63 (2021.01); H04W 12/64 (2021.01); H04W 12/71 (2021.01)] | 18 Claims |
|
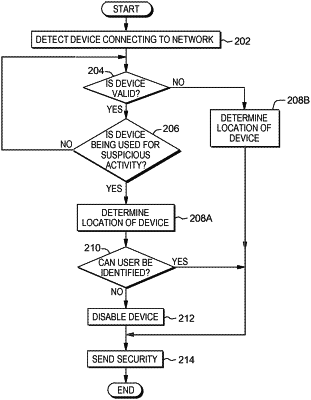
1. A method, comprising the steps of:
detecting, by one or more processors that a computing device has connected to a network;
determining, by the one or more processors, whether the computing device is valid,
based on determining that the computing device is valid, determining, by the one or more processors, whether the computing device is being utilized for one or more suspicious activities;
based on determining that the computing device is being utilized for one or more suspicious activities:
determining, by the one or more processors, a location of the computing device;
determining, by the one or more processors, whether a user of the computing device can be identified based on facial recognition;
based on determining that the user associated with the computing device cannot be identified, disabling the computing device; and
based on determining that the computing device is valid and is not being utilized for one or more suspicious activities, repeating the step of determining whether the computing device is being utilized for one or more suspicious activities until the computing device is no longer connected to the network.
|