| CPC H04L 63/0876 (2013.01) [H04L 9/3226 (2013.01); H04L 9/3239 (2013.01); H04L 63/083 (2013.01)] | 20 Claims |
|
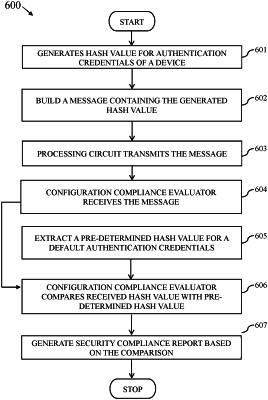
1. A method for verifying security compliance of one or more devices on a network, said method comprising:
receiving, by a server, a generated hash value from a processing circuit for configuration data of a device of the one or more devices on the network;
comparing, by the server, the hash value received from the processing circuit with a pre-determined hash value for said configuration data of said device, wherein the pre-determined hash value is based on a default password of said device, wherein the default password is set at the time of manufacture or installation of the device, wherein said device is determined as security non-compliant when the received hash value is equal to the pre-determined hash value, and said device is determined as security compliant when the received hash value is different than the pre-determined hash value;
in response to determining that the device is security non-compliant:
generating, by the server, a flag signal reporting the security non-compliance of the device;
providing an alert that the device is security non-compliant; and
displaying details of the device being security non-compliant, the details including the alert and an action to be taken;
in response to determining that the device is security compliant:
periodically comparing a new hash value for the configuration data of the device against an updated pre-determined hash value to determine whether the device remains security compliant; and
generating a report of a security compliance status of the one or more devices on the network.
|