| CPC H04L 45/745 (2013.01) [H04L 12/4641 (2013.01); H04L 45/02 (2013.01); H04L 45/42 (2013.01); H04L 2101/622 (2022.05)] | 17 Claims |
|
1. A computer-implemented method, comprising:
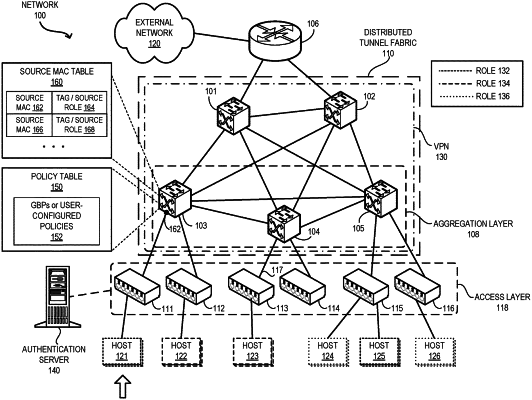
determining a first source media access control address (MAC) associated with a switch;
updating a MAC address table by mapping the first source MAC to a first tag which indicates a source role corresponding to a network infrastructure associated with the switch;
generating, by a processor associated with the switch, a first packet which indicates the first source MAC;
performing a first search in the MAC address table based on the indicated first source MAC to obtain the first tag;
performing a second search in a policy table based on the first tag for a group-based policy which indicates an action to be applied to the first packet;
responsive to determining that the second search is not successful, modifying a header of the first packet by adding the first tag to the header;
responsive to determining that the second search is successful, determining that the indicated action to be applied comprises allowing the first packet;
transmitting the first packet;
determining a second packet to be inspected by the processor;
receiving, by the processor, the second packet;
determining that the second packet is received over a virtual extensible local area network (VXLAN);
retrieving, from a header of the second packet, a second tag which indicates a source role corresponding to a sender of the second packet;
decapsulating the second packet to obtain an Ethernet header;
obtaining, from the Ethernet header, a second source MAC associated with the sender of the second packet; and
responsive to determining that the second source MAC is present in a cache:
determining a cached tag associated with the second source MAC in the cache;
determining that the cached tag does not match the second tag;
updating the cache by mapping the second source MAC to the second tag;
updating the MAC address table by mapping the second source MAC to the second tag; and
transmitting the second packet to a control plane daemon for processing.
|