| CPC H04L 41/0806 (2013.01) [H04L 41/20 (2013.01)] | 18 Claims |
|
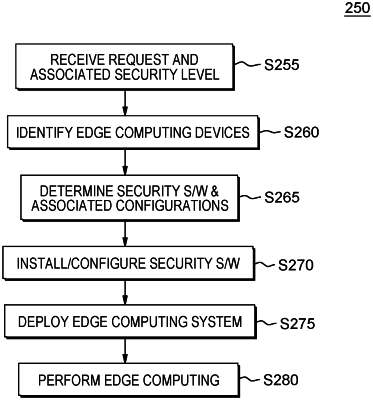
1. A computer-implemented method (CIM) comprising:
receiving, by a client edge device, a request to deploy computational work on the client edge computing device;
determining, by the client edge computing device, required security software that the client edge computing device must have to meet a predetermined level of security for securely performing the computational work on the client edge computing device;
instructing, by the client edge computing device, a vehicle-mounted secondary edge computing device that has the required security software to move into proximity of the client edge computing device;
subsequent to the vehicle-mounted secondary edge computing device moving into proximity of the client edge computing device, downloading the required security software from the vehicle-mounted secondary edge computing device to the client edge computing device;
installing the required security software on the client edge computing device; and
subsequent to the installation of the required security software on the client edge computing device, performing computational work on the client edge computing device.
|