| CPC H04L 9/0844 (2013.01) [H04L 9/3242 (2013.01); H04L 63/08 (2013.01)] | 20 Claims |
|
1. A computer-implemented method, comprising:
pre-storing a user authentication credential in an encrypted form on a companion application running on a second computing device, wherein pre-storing the user authentication credential comprises:
generating a fourth encrypted data by encrypting a third encrypted data having the user authentication credential using a mutual authentication key;
generating a fifth encrypted data by appending a second Message Authentication Code (MAC2) generated using the mutual authentication key to the fourth encrypted data; and
sending the fifth encrypted data to the second computing device via a communication channel;
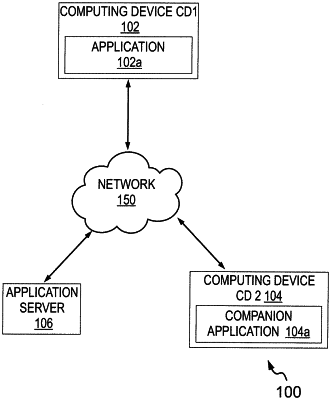
initiating, by a first computing device of a user, a detection of the second computing device of the user, the detection initiated based at least on an application requiring a user authentication credential to be entered, wherein the application is running on the first computing device and the user authentication credential is pre-stored in an encrypted form on a companion application running on the second computing device;
generating, by the first computing device, the communication channel with the second computing device, the communication channel generated based at least on generating the mutual authentication key by the first computing device and the second computing device;
sending, by the first computing device, a request to receive the user authentication credential to be entered on the companion application on the second computing device via the communication channel;
receiving, by the first computing device, the fifth encrypted data that includes the user authentication credential from the second computing device via the communication channel in the encrypted form;
decrypting, by the first computing device, the user authentication credential received in the fifth encrypted data; and
facilitating, by the first computing device, the entering of the user authentication credential on the application without user intervention.
|