| CPC G06F 21/606 (2013.01) [G06F 9/45558 (2013.01); G06F 13/24 (2013.01); G06F 13/28 (2013.01); G06F 13/4081 (2013.01); H04L 9/0819 (2013.01); G06F 2009/45587 (2013.01)] | 19 Claims |
|
1. A computer-implemented process for secure memory sharing between enclaves and virtual input/output adapters, the computer-implemented process comprising:
providing a system for performing a computer-implemented process for secure memory sharing between enclaves and virtual input/output adapters, wherein the system comprises a host, an enclave and an interrupt virtualization engine, wherein the host comprises a processor and a memory in communication with the processor to perform the computer-implemented process;
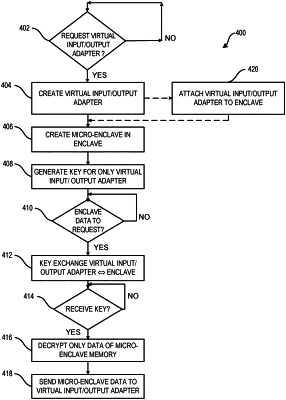
in response to a request for the enclave to create a virtual input/output adapter, creating a virtual input/output adapter associated with the enclave, wherein the enclave includes an enclave memory;
in response to receipt of an interrupt from within the system by the interrupt virtualization engine, routing the interrupt directly to the enclave, wherein the routing bypasses the processor;
creating by the enclave a non-sharable micro-enclave, to contain only data, nested within the enclave to use with the virtual input/output adapter, wherein the micro-enclave includes a non-zero portion of the enclave memory that is less that an entirety of the enclave memory, wherein the data of the non-sharable micro-enclave comprises at least one non-executable data segment, and wherein the at least one non-executable data segment comprises a portion of an object file, and creating a second non-sharable micro-enclave, to contain only data, nested within the enclave to use with a second virtual input/output adapter, wherein the second micro-enclave includes a non-zero portion of the enclave memory that is less than an entirety of the enclave memory;
generating a key by a memory encryption engine for the virtual input/output adapter for use by only the virtual input/output adapter; in response to a request to obtain data from the enclave by the virtual input/output adapter, exchanging the key with the non-sharable micro-enclave; in response to receiving the key, decrypting memory of only the non-sharable micro-enclave associated with the virtual input/output adapter to obtain the data; and sending the data from the non-sharable micro-enclave nested within the enclave to the virtual input/output adapter.
|