| CPC G06F 21/561 (2013.01) [G06F 21/566 (2013.01); G06F 2221/034 (2013.01)] | 21 Claims |
|
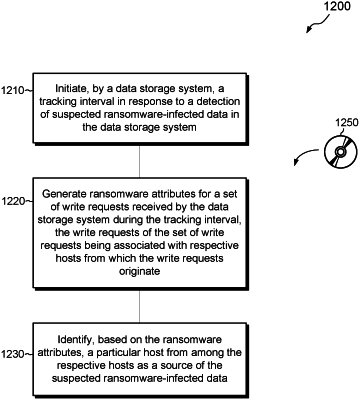
1. A method of identifying hosts suspected of being sources of ransomware infection, comprising:
initiating, by a data storage system, a tracking interval in response to a detection of suspected ransomware-infected data in the data storage system;
generating ransomware attributes for a set of write requests received by the data storage system during the tracking interval, the write requests of the set of write requests specifying respective initiators and being associated with respective hosts from which the write requests originate; and
identifying, based on the ransomware attributes, a particular host from among the respective hosts as a source of the suspected ransomware-infected data,
wherein the method further comprises (i) tagging datasets specified by the set of write requests with identifiers of the respective initiators, (ii) associating ransomware attributes with the respective initiators based on the tagging, and (Hi) identifying a set of initiators for which the associated ransomware attributes indicate a suspected ransomware infection.
|