| CPC G06F 3/0622 (2013.01) [G06F 3/0638 (2013.01); G06F 3/0655 (2013.01); G06F 3/0673 (2013.01)] | 20 Claims |
|
1. An apparatus, comprising:
a memory array;
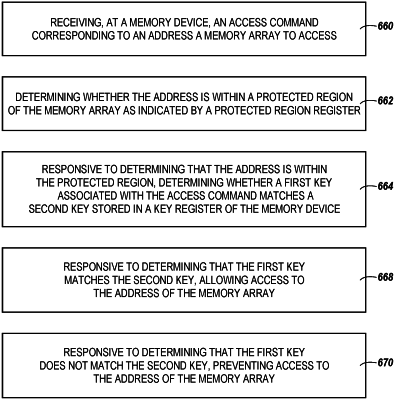
a key register configured to store a first key used to determine whether access commands are allowed access to a protected region of the memory array;
a protected region register configured to store addresses defining the protected region;
an access count register to store an access count;
a mode register; and
control circuitry configured to:
responsive to receiving a security mode initialization command from a host:
store the first key in the key register;
store a first address corresponding to the memory array in the protected region register, wherein the first address is a protected address and the first key corresponds to the protected address;
responsive to storing the first key and storing the first address, set the mode register to a locked mode;
responsive to determining that the mode register is in the locked mode, determine whether the access count is less than a threshold;
responsive to determining that the access count is less than the threshold, determine whether to allow access to a second address corresponding to an access command based on whether the second address is within the protected region and based on whether a second key from a number of keys corresponding to the access command from a number of access commands matches the first key stored in the key register, wherein each key of the number of keys is provided with a different access command of the number of access commands; and
responsive to allowing access to the second address, increment the access count register and enable a row driver;
reset the access count register responsive to a lapse of time without receiving additional access commands to the protected region.
|