| CPC H04W 12/35 (2021.01) [H04W 12/088 (2021.01); H04W 12/102 (2021.01)] | 20 Claims |
|
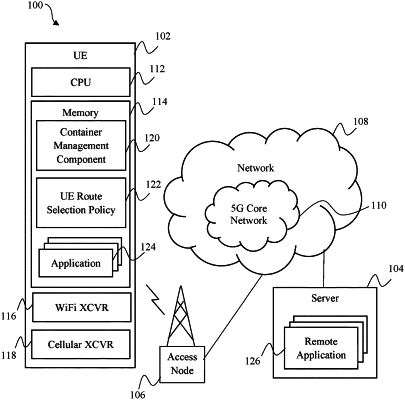
1. A method of user equipment (UE) implemented network slice security protection, comprising:
receiving, by the UE, a first request to initialize a first application on the UE;
in response to receiving the first request, performing, by the UE, a first query of a UE Route Selection Policy (URSP) stored on the UE based on the first application, wherein the URSP comprises a plurality of traffic descriptors and a plurality of security descriptors;
in response to the first query, receiving, by the UE, traffic descriptors and security descriptors associated with the first application, wherein the traffic descriptors associated with the first application identify a first network slice to be used by the first application, and wherein the security descriptors associated with the first application comprise a first security flag indicating that the first network slice is not secure;
binding, by the UE, traffic for the first application to a protocol data unit (PDU) session based on the traffic descriptors associated with the first application;
communicating, by the first application, with a core network via the first network slice;
receiving, by the UE, a second request to initialize a second application on the UE;
in response to receiving the second request, performing, by the UE, a second query of the URSP stored on the UE based on the second application;
in response to the second query, receiving, by the UE, traffic descriptors and security descriptors associated with the second application, wherein the traffic descriptors associated with the second application identify a second network slice to be used by the second application, and wherein the security descriptors associated with the second application comprise a second security flag and a virtualization container ID;
initiating, by the UE based on the second security flag indicating that the second network slice is secure, the second application within a virtualization container corresponding to the virtualization container ID, wherein the virtualization container is bound to the second network slice;
binding, by the UE, traffic for the second application in the virtualization container to a PDU session based on the traffic descriptors associated with the second application; and
communicating, by the second application executing within the virtualization container, with the core network via the second network slice bound to the virtualization container.
|