| CPC H04L 63/20 (2013.01) [G06F 9/542 (2013.01); G06F 21/552 (2013.01); G06F 21/554 (2013.01)] | 17 Claims |
|
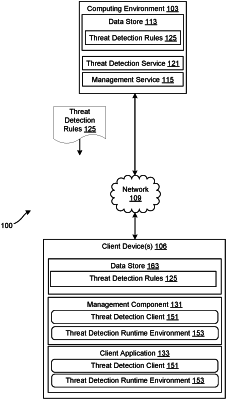
1. A system for detecting a compromised device, comprising:
a client device comprising at least one hardware processor; and
program instructions executable in the client device that, when executed, direct the client device to:
detect a launch condition associated with a threat detection runtime environment, the program instructions being embedded within the application;
retrieve one or more rules from a remotely executed service, the rules specifying how to determine that the client device has been compromised;
execute the threat detection runtime environment within the application;
register an event handler within the threat detection runtime environment based upon the rules, the event handler configured to detect a condition specified by the rules indicating a compromised state; and
detect, using the event handler, the condition by listening for a response to a command executed on the client device that is initiated by the threat detection runtime, wherein the command obtains a property of a file stored on the client device.
|