| CPC H04L 63/20 (2013.01) [G06F 16/2477 (2019.01); G06F 16/951 (2019.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01)] | 4 Claims |
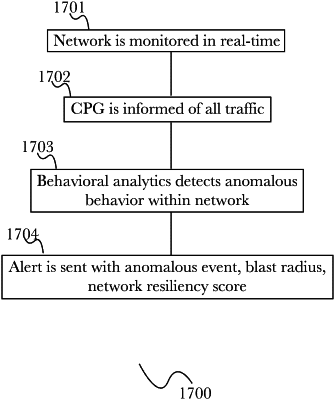
|
1. A system for cybersecurity profiling and rating using internal and external reconnaissance, comprising:
a cyber-physical graph module comprising a first plurality of programming instructions stored in a memory of, and operating on a processor of, a computing device, wherein the first plurality of programming instructions, when operating on the processor, cause the computing device to create a cyber-physical graph of an organization, the cyber-physical graph comprising nodes representing entities associated with the organization and edges representing relationships between entities associated with the organization;
a reconnaissance engine comprising a second plurality of programming instructions stored in the memory of, and operating on the processor of, the computing device, wherein the second plurality of programming instructions, when operating on the processor, cause the computing device to:
perform a reconnaissance search using the cyber-physical graph; and
apply some or all of the results of the reconnaissance search to the cyber-physical graph to create a cybersecurity profile of the organization; and
a scoring engine comprising a third plurality of programming instructions stored in the memory of, and operating on the processor of, the computing device, wherein the third plurality of programming instructions, when operating on the processor, cause the computing device to:
receive the cybersecurity profile and the results of the reconnaissance search;
using the cyber-physical graph and the reconnaissance search results:
estimate a frequency and severity of cyber-attacks on the organization;
identify a plurality of cybersecurity risks associated with the organization;
determine a business impact for each cybersecurity risk identified;
assign a network resilience rating to the organization; and
determine a functional cybersecurity score for the organization based at least on the network resilience rating.
|