| CPC H04L 63/20 (2013.01) | 21 Claims |
|
1. A computer-implemented method for mitigating cyber security risk of an enterprise network, the computer-implemented method comprising:
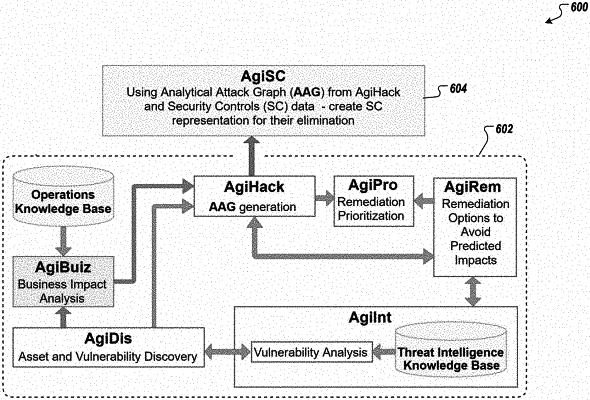
receiving an analytical attack graph (AAG) representing paths within the enterprise network with respect to at least one target asset, the AAG at least partially defining a digital twin of the enterprise network and comprising a set of rule nodes, each rule node representing an attack tactic that can be used to move along a path;
determining a set of security controls, each security control mitigating at least one rule node in at least a sub-set of rule nodes of the set of rule nodes;
executing a first iteration of a simulation representing implementation of a first sub-set of security controls in the enterprise network, the first iteration comprising:
for each security control in the set of security controls, determining, a first influence score that represents a change in a security risk that would result from implementing the security control and a rule distribution representing one or more rules that the security control mitigates,
defining the first sub-set of security controls based on the first influence scores, and
reducing the AAG based on the first sub-set of security controls and a first reduction method to provide a first residual AAG, the first reduction method being automatically selected based on a curve representative of an influence score histogram for the set of security controls;
determining a decrease in a graph risk value based on the AAG and the first residual AAG; and
selectively implementing the first sub-set of security controls in the enterprise network at least partially in response to the decrease in the graph risk value.
|